We’ve gotten pretty “Techy” recently, explaining:
- SQL Injection: Made Simple 💉
- AWS Attack Made Simple: whoAMI 💀
- Weekend Project: DevSecOps Intro🛠️
Let’s roll it back for beginners - As far as i’m aware a lot of you are really just interested in the Cloud and maybe haven’t actually ever interacted with it…
Feel free to skip straight to the project below this networking primer…
What is Networking?
Chances are you already have a picture in your head of what computer networking is. To put it simply, it’s the practice of connecting computers and other devices to share resources and information. You can introduce hardware into your network (like routers, switches, and cables) and software (such as network protocols and operating systems) to enable communication between devices. Networks can range from small home setups (Your router to your phone) to vast global systems like the Internet, allowing devices to share data, access remote resources, and talk to each other.
Let’s actually start understanding what makes up a network
As always I want to keep it as straightforward as possible, so we’ll start with the key terms and definitions.
Network: A group of interconnected devices (such as computers, printers, and servers) that share resources and communicate.
LAN (Local Area Network): A network that connects devices within a limited area, such as a home, office, or building.
WAN (Wide Area Network): A network that spans a large geographical area, often composed of multiple LANs. The internet is the largest WAN.
Switch: A device that connects devices within a LAN, directing data to its destination within the network.
Firewall: A security device or software that monitors and controls incoming and outgoing network traffic based on predetermined security rules.
SSID (Service Set Identifier): The name of a wireless network, allowing users to identify and connect to a specific Wi-Fi network.
MAC Address (Media Access Control Address): A unique identifier assigned to a network interface card (NIC) for communication on the physical network segment.
VPN (Virtual Private Network): A technology that creates a secure, encrypted connection over a less secure network, such as the internet. VPNs are commonly used to ensure privacy and security for users accessing a network remotely.
DNS:
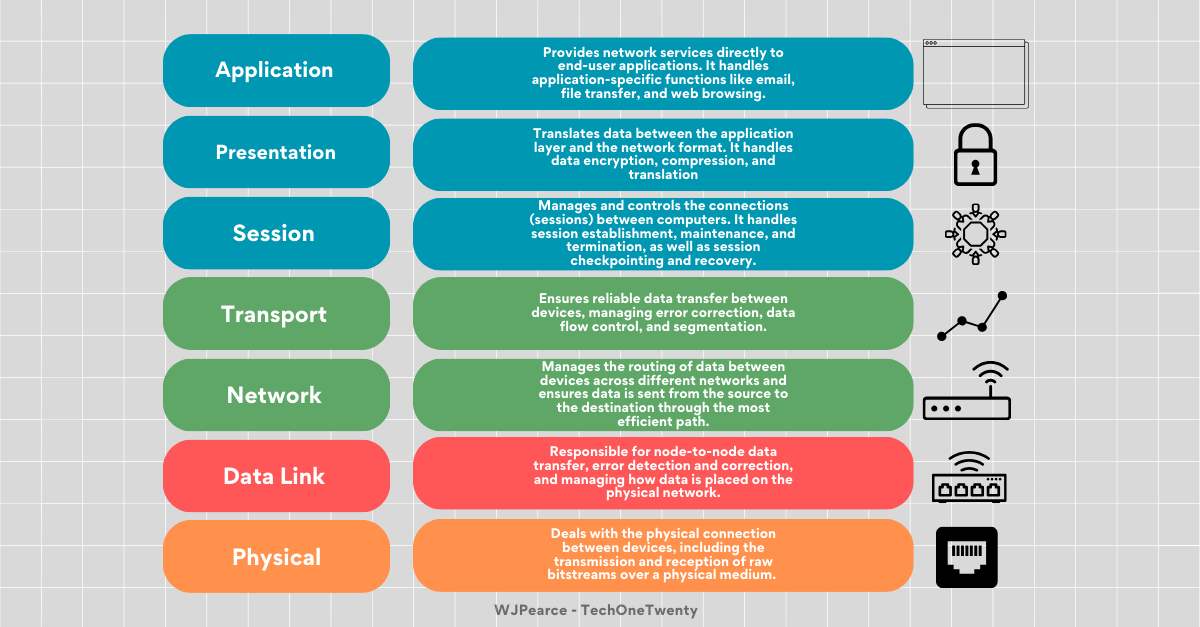
TCP/IP Model & OSI Model
The last thing we need to cover here before we can move on to the Real-world Example is the OSI Model and TCP/IP model. These two models are fundamental to understanding how computer networks operate and data flow.
OSI Model
TCP/IP
Why These Models Matter?
Understanding the OSI and TCP/IP models is important because they provide a structured approach to network communication. They help us break down complex network processes into manageable pieces, making designing, troubleshooting, and understanding how data moves across a network easier. Whether you're dealing with local area networks (LANs), wide area networks (WANs), or the internet itself, these models serve as the foundation for all networked communication.
Basic AWS Networking Project
This is a VERY gentle introduction to networking in the cloud…It serves as a fundamental demonstration of network communication principles.
By configuring two AWS instances within the same VPC and adjusting the security group of Instance B to allow traffic from Instance A, you're laying the groundwork for understanding how resources communicate securely. I think it's essential to understand the significance of these actions, observe how the CIDR ranges are configured and how being within the same VPC allows for seamless communication without traversing the public internet.
These are the building blocks of networking, and mastering these basics will enable you to design more complex and secure network topologies. Take the time to explore and understand what's happening in this setup, as everything in networking builds on these core concepts
If you are unsure of how to Launch any resources in this section, they are all covered in the cloud security project in TechOneTwenty.
Step One: Create a VPC
Give it a meaningful name and IP Range
Note: Private IP ranges in an AWS VPC refer to non public IP addresses used within your virtual network to allow resources like EC2 instances to communicate securely. These IPs fall within the standard RFC 1918 ranges: 10.0.0.0/8, 172.16.0.0/12, and 192.168.0.0/16. They're not routable over the internet and are ideal for internal traffic, helping you isolate and control access within your cloud environment.
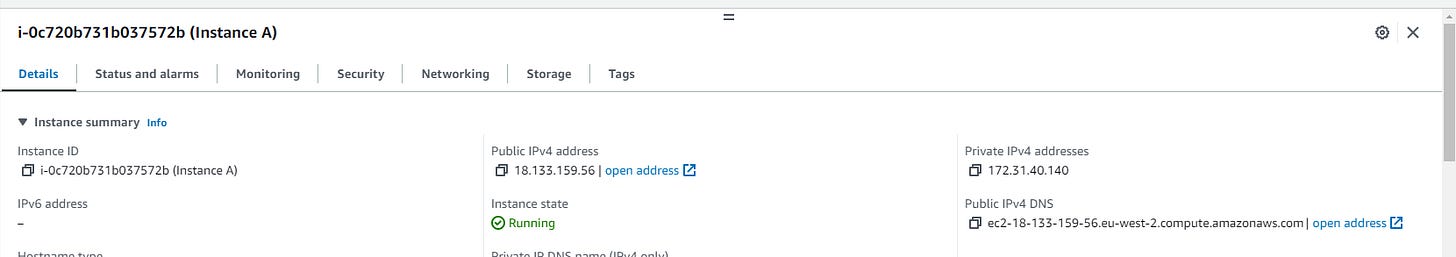
Step Two: Within your VPC Launch, Two Instances
I have named mine Instance A and B
Take a look at the private IP addresses
+
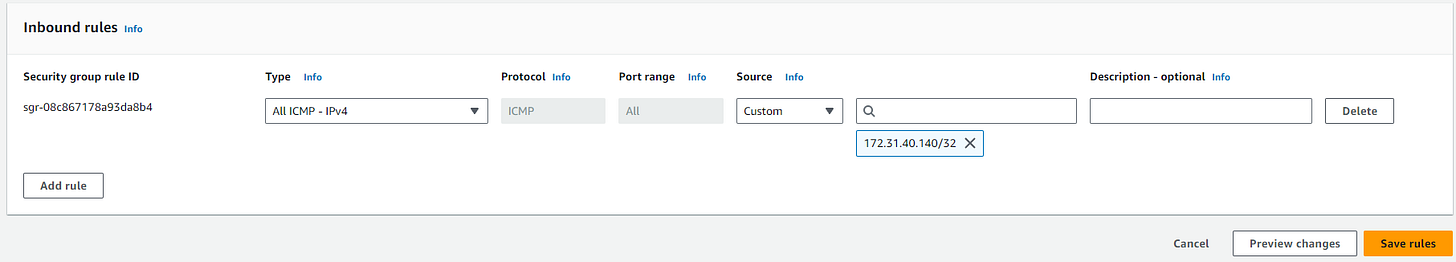
Step Three: Amend the Security Group of Instance B
Allow ICMP (ping) traffic from Instance A to Instance B
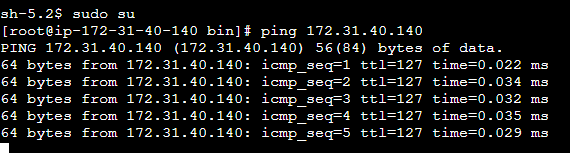
Step Four: Connect to Instance A and ensure Instance B is reachable
Use the Ping Command
Note: You’ll need either Session Manager configured here or have pre set-up your SSH keys.
Ping 172.31.38.10Congrats 🎉 Instance A and Instance B can now communicate!
Did you like this? Read on…
This was a project from TechOneTwenty: A Practical Breakdown: Understanding Cloud & Security with simple projects you can do at home
It’s actually on sale right now 💸 Click the image to check it out🖱️
Thank you for reading: Keep it secure, keep it light-hearted!
WJPearce - CyberBrew