Heads up this one might no fit entirely in your inbox…
I was recently chatting with one of my readers, helping them practice some basic cybersecurity interview questions.
Things were going well until it came to explaining basic vulnerabilities, their confidence wavered.
If that sounds familiar, don’t worry. By the end of this newsletter, you'll have a solid grasp of one of the oldest web application vulnerabilities out there.
SQL Injection: Simply Explained
Before we dive into the fun stuff, actually using SQL Injection, we need to take a step back and understand two key concepts:
SQL
Three-tier Web Application Architecture
Trust me, getting comfortable with these fundamentals is what sets apart average engineers from great ones. So, let’s break it down.
Let’s start with the basics. SQL stands for Structured Query Language, and it’s the language we use to interact with databases.
With SQL, you can:
Just Quickly: If you like these break downs with diagrams and easy explainers, I invite you to join my community and gain access to my history of Cloud Security Weekend Projects
These operations are often called CRUD.
So let’s look at some basic SQL Syntax and start by writing out our first query
Breaking that down we have the 3 key words here:
SELECT– Retrieves specific columns or all (*) from a table.FROM– Specifies which table to query data from.WHERE– Applies conditions to filter results.
Effectively SQL queries are like asking the database a question.
SELECT
FROM
WHERE
Stick with me just one more quick topic to cover and we can get into the fun part 😉
Modern web applications are programs you can access directly from your browser or mobile app. Think of platforms like Gmail, Instagram, or YouTube.
These apps allow you to do things like send emails, share photos, or manage user accounts - all by interacting with data stored in a database.
Most modern web apps follow what’s called a Three-Tier Architecture. It’s like a relay system, where data flows between layers.
Frontend (Client Layer) – The user interface
Backend (Application Layer) – Processes requests and business logic
Database (Data Layer) – Stores information
Working all together like this:
And finally:
💉 SQL INJECTION 💉
Awesome job sticking with me! I know diving into the fundamentals can feel slow at times.
And now, the moment you’ve been waiting for: SQL Injection.
Let’s imagine a login page. At first glance, it seems simple enough, just a username and password box. You’ve seen this a million times before. But beneath the surface, this seemingly innocent form can hide a serious vulnerability 💀
Here’s how attackers exploit it using SQL Injection.
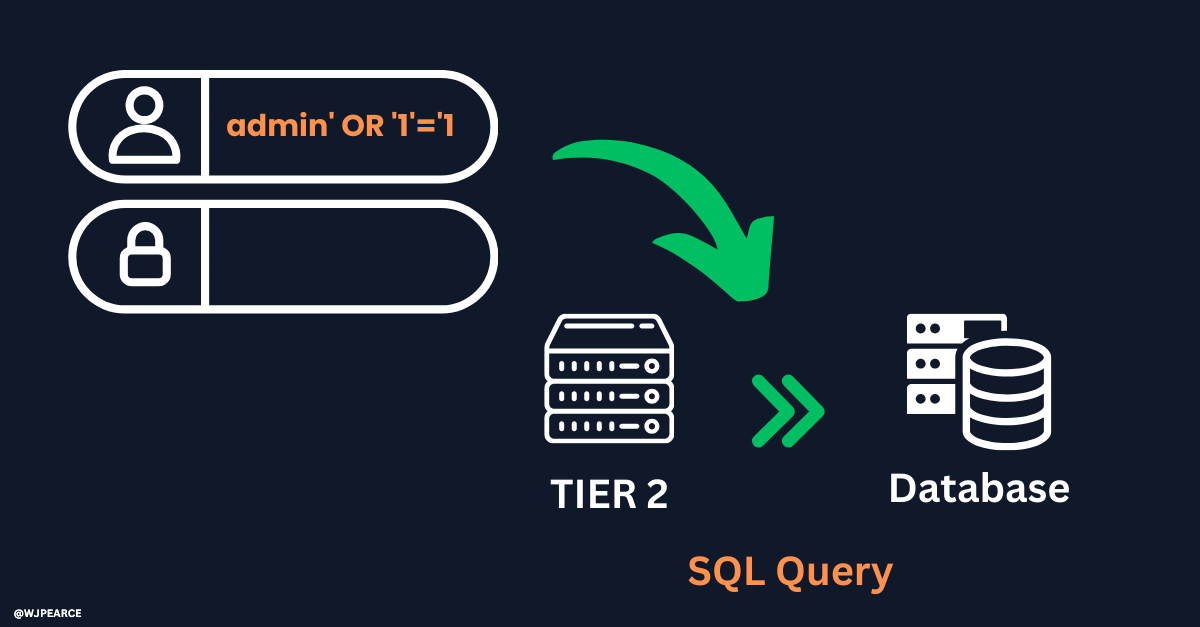
Let’s start by guessing the password. We’ll try the username admin and the password PASSWORD123.
When we type in these credentials and hit submit, here’s what happens behind the scenes:
The input gets sent to Tier 2, the backend server. The backend translates the input into a SQL command that checks the database.
The database looks up the username and password in the users table. If the condition evaluates to true: Meaning the username and password match, the system grants access.
But in this case, the credentials don’t match, so it denies access.
Here’s where things get interesting.
Looking at the SQL command, we notice that user inputs are wrapped in single quotes ('). In SQL, anything inside single quotes is treated as a string - a data type used to represent text.
But what happens if we try entering just a single quote (') as our input?
This time, instead of a login attempt, we’d receive a syntax error.
Why is this great news? 🥳
A syntax error suggests the possibility of a SQL Injection vulnerability but does not confirm it. We are assuming it does in this case. The single quote disrupted the SQL query, revealing that the input wasn’t properly “sanitized”.
We now understand that user input directly affects the SQL query. That means if we manipulate the input correctly, we might be able to bypass authentication altogether.
Instead of guessing the password, let’s try an injection attack by crafting an input that always evaluates as true
Here’s what we’ll enter:
Username:
admin' OR '1'='1Password:
password123
Now, let’s break down what happens behind the scenes. The SQL query the backend generates might look something like this:
This of course gets executed on the backend
At first glance, it might seem like '1'='1' would always return TRUE and grant access. However, while '1'='1' does make the username condition always true, the presence of AND means that the database still requires the correct password.
Because AND has a higher precedence than OR, the database does not simply grant access based on the OR condition alone.
Like so:
Because of this, the database interprets the query like this:
Now, let’s break it down:
1️⃣ 1'='1' is always true, but because AND has higher precedence than OR, the database first checks whether the password is correct before evaluating the OR condition.
⏸️This means our attempt fails unless we provide the correct password. ⏸️
2️⃣ The database only grants access if the password is actually password123, which causes the injection attempt to fail unless the correct password is known.
Well how do we make this work then? 🤔
So far, we’ve seen that the initial injection attempt fails due to the precedence of AND, which still requires a correct password. But what if we modify our input to completely remove the password condition?
Here’s a better injection attempt:
Pssst: We are assuming the username is admin here
Why Does This Work?
The
--sequence is an SQL comment.Anything after
--is ignored by the database.This completely removes the password check.
The actual SQL query executed becomes:
Since everything after -- is ignored, the query only checks if the username exists.
And just like that, we’ve bypassed authentication and logged in as the admin! 🎉 🎉 🎉
Now, this is what I’d call level one SQL Injection. Straightforward and easy to understand. The chances of seeing this exact scenario in the wild today are rare, but it does still happen, especially in poorly secured systems or legacy applications.
On a scale of:
🟢 "I LOVED that!" → 🔴 "WTF did I just read?"
Do you enjoy this kind of deep technical breakdown? Let me know! 🤓🔥
Thank you for reading: Keep it secure, keep it light-hearted!
WJPearce - CyberBrew
Cyber Notes is as affordable as Substack allows! I put in hours of work crafting weekend deep dives and technical explainers - most of them for free. Your support keeps this going and means the world. 🚀 Subscribe now!

































Absolutely love the breakdown , 👍
The last ten years of my career was mainly TSQL programming so scary to think there are sites out there still vulnerable to this kind of attack. I’m thinking there must be a number of second and third world parties that are at risk if the educational and technical infrastructure is not well established. Also anywhere the oversight is poor or tyrannical. I say the last because I once had a boss who, although not trained in any aspect of IT, used to look things up on the web and spring tests on us with no warning. Three fails and you got the sack. We lost a number of good staff before we all got new jobs and left him to his own devices.