This project is a chapter from TechOneTwenty: A Practical Breakdown: Understanding Cloud & Security with simple projects you can do at home
You can check it out here! TechOneTwenty 📖
Feel free to skip straight to the Project 🔑🔥 - it’s a really fun one!
What is Hashcat?
Hashcat is probably the tool on this list that comes to mind when you think of cybersecurity. It’s often associated with “script kiddies” and those super weird AI-voiced YouTube videos. However, it's important to say that Hashcat is also highly respected among professionals for legitimate password recovery and security testing purposes. It’s tools like Hashcat that first spark people's interest in cybersecurity; it’s tools like this that start careers.
But what actually is it?
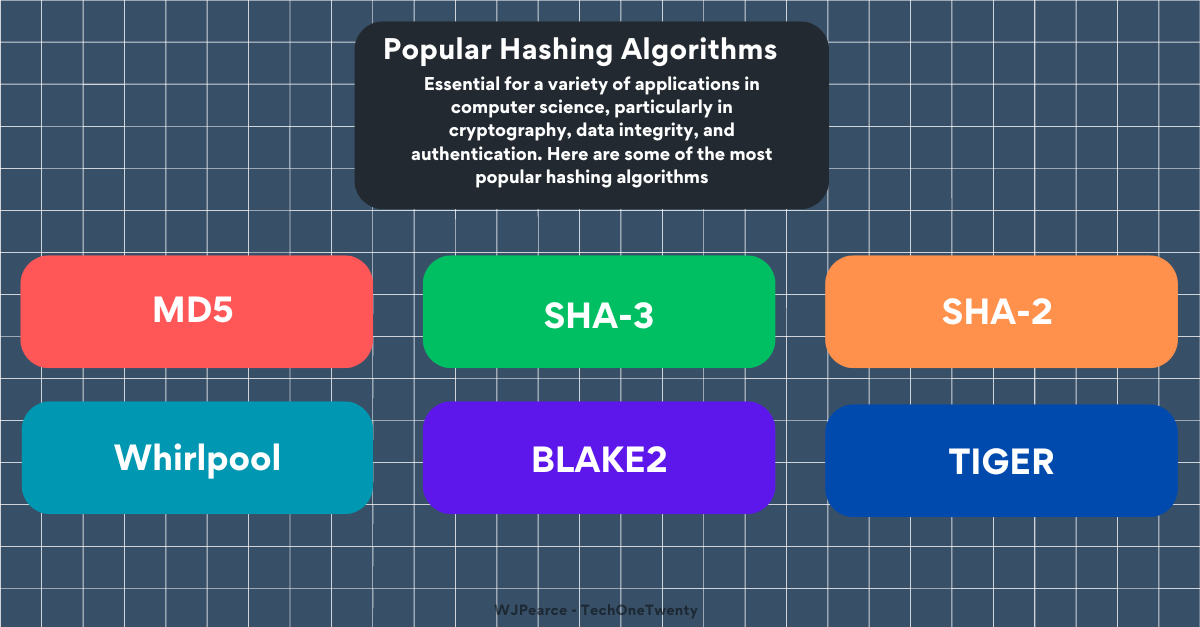
Hashcat is a powerful password recovery tool that uses the power of your computer's GPU to crack passwords efficiently, as if you needed another reason to buy a new GPU. It supports many hashing algorithms, including MD5, SHA-1, and many others commonly used to secure passwords. It uses different techniques to do this: brute-force, dictionary, rule-based, and hybrid attacks. Hashcat can systematically guess and test password combinations until it finds a match.
The tool's flexibility is another reason for its popularity. Hashcat is open-source and works on most operating systems, including Windows, macOS, and Linux. It’s handy because you can customise attacks using different modes and options to optimise performance and target specific weaknesses.
Additionally, Hashcat supports distributed cracking, allowing multiple computers to work together on a single password hash, significantly reducing the time required to crack complex passwords.
Core Knowledge
Let’s take a look at the process Hashcat goes through when running, and break down what you need to know.
Hash Identification: Hashcat begins by identifying the type of hash it needs to crack. You have to specify the hash type manually using a specific mode ( -m 0 for MD5, -m 1400 for SHA-256). This is necessary for Hashcat to know how to process the hash correctly.
Input Selection: The user selects the type of attack to perform. Common attack types include brute-force attacks, dictionary attacks, and rule-based attacks. For example, a dictionary attack uses a predefined list of possible passwords, while a brute-force attack tries all possible combinations within a specified range.
Optimisation and Configuration:
While Hashcat includes features like automatic GPU tuning, to achieve the best performance, you need to fine-tune the settings manually. Hashcat does not automatically configure itself to the "maximum potential" of your hardware; instead, it requires user intervention to unlock its full capabilities.
Processing and Cracking:
Hashcat starts the cracking process by systematically generating and hashing candidate passwords. It compares each generated hash with the target hash. Depending on the attack mode, it might apply various rules or combinations to enhance the guessing process.
Match and Output:
When Hashcat finds a hash that matches the target hash, it outputs the corresponding plaintext password. This result is logged for the user, and Hashcat can either stop or continue to search for additional matches if required.
By breaking down the password recovery process into these stages, Hashcat narrows down the possible password candidates and expedites the discovery of the correct password.
Before we get hands-on with Hashcat, we should take the time to understand some key terms.
There are a few key terms that you might not be familiar with. Here's a breakdown of them before we launch Hashcat:
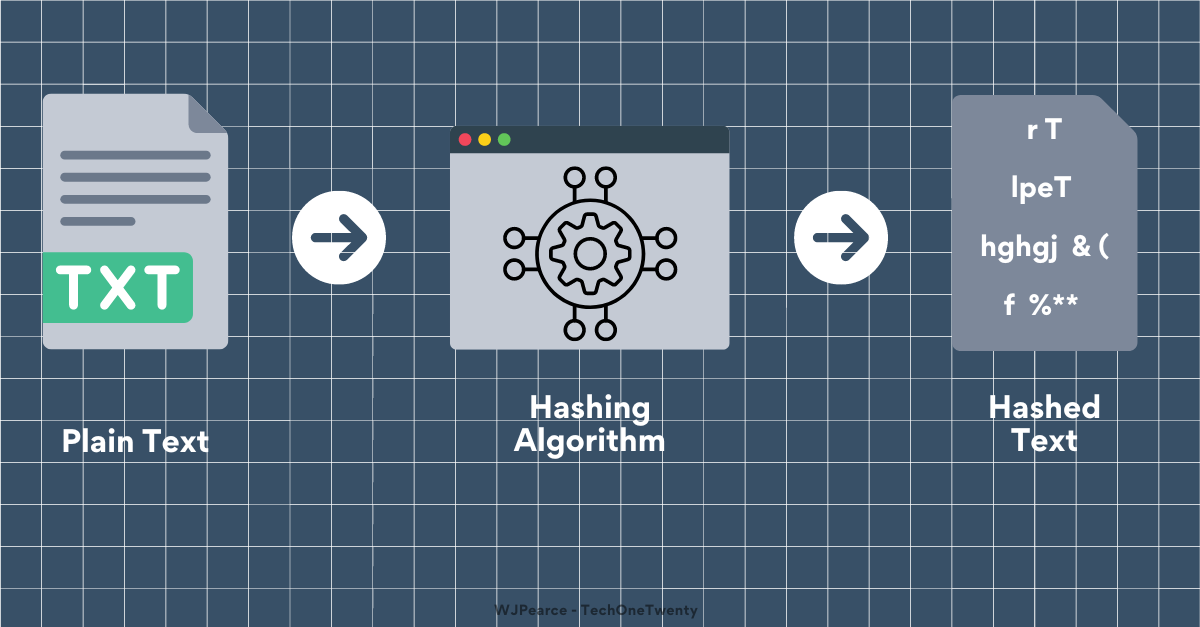
Hash: A fixed-length string or value generated from a plaintext input using a hash function, often used for storing passwords securely.
Wordlist: A file containing a list of potential passwords used in dictionary attacks to guess the hashed passwords.
Salt: Random data added to a password before hashing to make it more difficult for attackers to use precomputed hash tables.
MD5: A widely used cryptographic hash function that produces a 128-bit hash, though it is now considered insecure due to vulnerabilities.
Mode: Refers to the type of attack being performed (straight, combinator, brute-force, etc.).
Benchmarking: The process of testing and measuring the performance of Hashcat on a specific system or with specific hash types.
Rules: Modifications applied to words in a wordlist to create variations, increasing the chances of cracking passwords with small changes.
Potfile: A file used by Hashcat to store cracked passwords so they are not attempted again in future sessions.
Session: A saved state of a Hashcat cracking attempt that can be resumed later, useful for long-running attacks.
Hashcat Setup:
Boot up your virtual machine - Kali Linux or Parrot OS would be ideal here. Open the terminal, and if you’ve not opened your VM in a while, you may need to run the following:
sudo updatedb.plocateYou can double-check that you have Hashcat installed by running:
hashcat --versionReal-World Example ~ Micro Project
Let’s get into it. We have our VM, a fresh version of Hashcat, and a clean terminal ready to go.
Remember, if you are ever unsure about how to use a tool or the options you can configure it with, make use of the help command; we can use it here by typing:
Keep reading with a 7-day free trial
Subscribe to Cyber Notes to keep reading this post and get 7 days of free access to the full post archives.